Quantum computing is a present-day actuality that’s altering cybersecurity in basic methods. The encryption defending our most delicate information at the moment received’t stand an opportunity towards highly effective quantum assaults. This implies organizations ought to start adopting post-quantum cryptography (PQC) options now to safe their information in transit. And since wide-area networks (WANs) carry a lot mission-critical information, they’re floor zero. This weblog takes a take a look at key issues for establishing quantum-safe safety in WAN infrastructure.
The quantum risk panorama and its affect on WAN safety
Our present safety depends on classical encryption, particularly public-key strategies. However these are susceptible to quantum assaults. Think about a robust cryptographically related quantum laptop (CRQC) designed to interrupt at the moment’s encryption.
This results in a frightening situation referred to as harvest now, decrypt later (HNDL).
Right here’s the way it works: An attacker secretly copies your encrypted information and the general public key info because it travels throughout your community. When a CRQC turns into out there, it’s used to derive the personal key. With each the general public and quantum-calculated personal key, the session key can then be unlocked, and all that delicate, beforehand captured information might be decrypted. This implies any information you ship at the moment might be uncovered tomorrow.
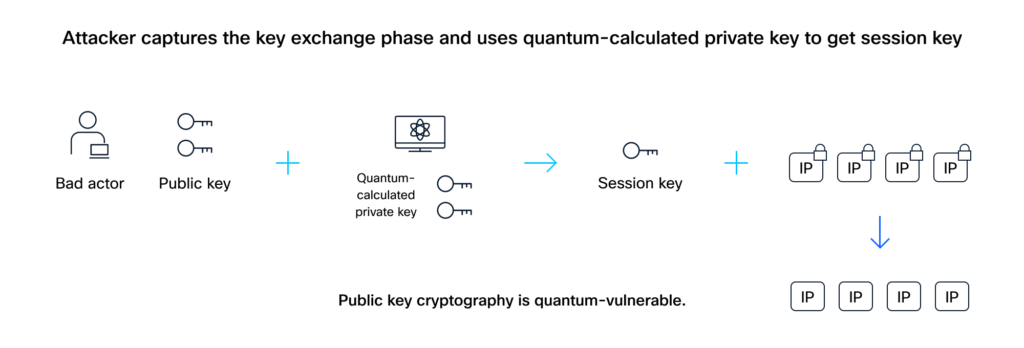

Your WAN wants quantum-safe safety first
Your WAN is the spine that connects information facilities, department places of work, and cloud environments. It carries your most delicate info, usually information that should keep confidential for years. Securing this site visitors towards quantum threats is crucial for stopping future breaches and staying compliant.
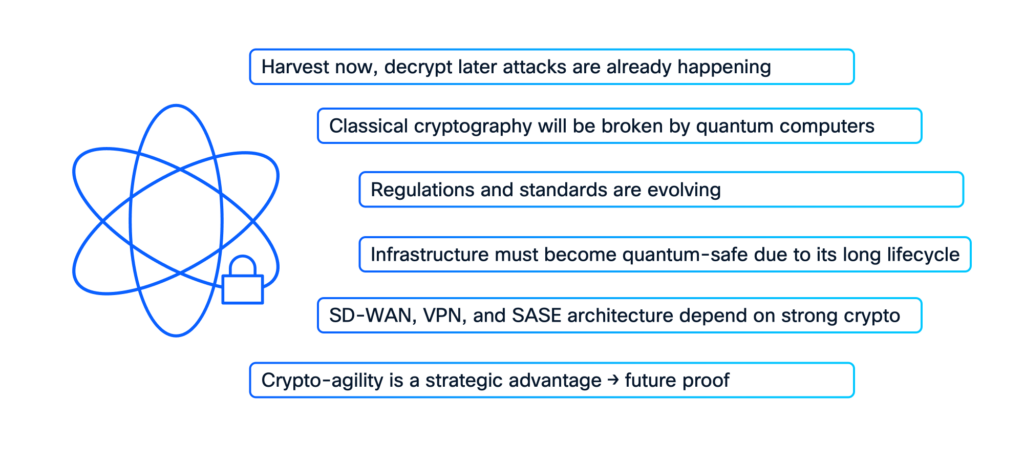
Right here’s why a WAN-first strategy to PQC is smart:
- WAN site visitors usually has a protracted shelf life for confidentiality. Its journey throughout numerous transports between distant websites and information facilities makes it a super goal for HNDL assaults.
- As we speak’s classical encryption strategies, particularly these counting on the issue of factoring massive numbers, are immediately threatened by quantum algorithms like Shor’s.
- International regulatory our bodies are already issuing pointers for defending towards quantum-enabled assaults. Starting along with your WAN helps you get forward of compliance necessities and cut back danger sooner.
- Your WAN edge routers are effectively positioned to implement new quantum-safe encryption. Choosing the proper infrastructure ensures PQC expertise gives complete protection.
- Trendy options like SD-WAN, digital personal community (VPN), and safe entry service edge (SASE) are constructed on sturdy cryptography. PQC is a pure evolution of this foundational safety.
- The centralized nature of WANs makes them well-suited for rolling out hybrid encryption by mixing previous and new cryptographic strategies. This agility will simplify your migration to a completely quantum-safe future.

Constructing a complete post-quantum safety (PQS) technique
Publish-quantum safety (PQS) is about upgrading cryptographic algorithms, protocols, and whole techniques to face up to quantum assaults.
A very efficient PQS resolution have to be complete, specializing in three key areas:
- Encryption: Protects your information in transit from HNDL assaults.
- Authentication: Ensures solely respectable customers and units can entry your community.
- Safe boot: Helps make sure the integrity and authenticity of your system’s startup course of.
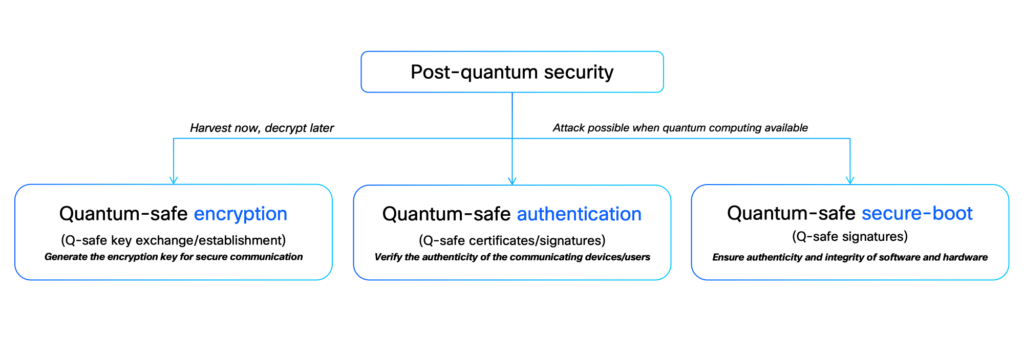

Whereas the precise timeline for a CRQC is unsure, being proactive is essential. An entire PQS technique ought to handle all these dimensions, defending your information and infrastructure from each angle.
Shield your WAN from quantum assaults
There are two essential approaches to creating your WAN quantum-resistant:
Publish-quantum pre-shared key (PPK): This methodology provides quick safety towards HNDL assaults. A PPK is a particular key that’s combined along with your classical IPsec session key. Since an attacker can not seize this PPK, even a CRQC can’t work out the true session key. You may arrange PPKs manually or use a quantum key distribution (QKD) system to acquire them. This protects your crucial information proper now.
Publish-quantum cryptography ( PQC) algorithms: This methodology entails adopting new, quantum-safe algorithms. Requirements our bodies just like the Nationwide Institute of Requirements and Expertise (NIST) are quickly approving these. For instance:
- ML-KEM (FIPS-203): For quantum-safe key alternate (encryption)
- ML-DSA (FIPS-204): For quantum-safe digital signatures (authentication)
- LMS (NIST SP 800-208): For guaranteeing the quantum-safe integrity of firmware and software program at a system degree (safe boot)
Cisco 8000 Sequence Safe Routers: Your quantum-safe WAN resolution
The Cisco 8000 Sequence Safe Routers are particularly designed for the quantum period, offering strong, quantum-safe WAN connectivity throughout department places of work, campuses, and information facilities.
These routers are constructed with highly effective crypto engines. They’ll deal with demanding PQC algorithms with out slowing down your community. Excessive-end fashions function the Quantum-Move Processor (QFP) ASIC whereas department and campus routers use a brand new safe networking processor ASIC. Each are optimized for high-throughput crypto offload.


For quick quantum-safe encryption utilizing the PPK methodology, Cisco 8000 Sequence Safe Routers help Safe Key Integration Protocol (SKIP) and RFC 8784, which permit the blending of a pre-shared key into the IKEv2 key alternate. The PPK might be realized from QKD techniques, or if QKD isn’t out there, PPKs might be configured regionally within the machine configuration. This resolution allows quantum-safe encryption for IKEv2 IPsec connectivity.
With native PQC options, Cisco 8000 Sequence Safe Routers will help hybrid encryption. This implies you’ll be able to mix an present legacy encryption secret with a brand new, NIST-approved quantum-safe methodology’s shared secret throughout the similar crypto information airplane. Primarily based on RFC 9370, this hybrid strategy cryptographically blends a number of shared secrets and techniques to create a stronger session key. The hybrid implementation allows clean migration and lets you implement ML-KEM algorithms as wanted. All public key cryptography options, together with IKEv2 IPsec, SD-WAN, FlexVPN, DMVPN, IKEv2 Cluster Load-balancing, MACsec with EAP-TLS, SSH, and extra, will supply native PQC encryption capabilities on the Cisco 8000 Sequence Safe Routers.
The Cisco 8000 Sequence Safe Routers are foundational for constructing a quantum-safe encryption resolution in your community.
Act now for a quantum-safe future
Quantum computing is not a distant risk; it’s right here, demanding quick motion to guard our digital world. Organizations have to proactively improve their community infrastructure, particularly their WANs, to defend towards quantum assaults.
The transfer to PQC is an pressing step to protect towards threats like HNDL. By prioritizing quantum-safe options in your WAN, you’ll be able to guarantee long-term information confidentiality, meet regulatory calls for, and preserve operational integrity.
Cisco 8000 Sequence Safe Routers are purpose-built for this problem. They provide each quick safety with PPK and a transparent path to native PQC strategies, securing your information in transit and important infrastructure.
Investing in quantum-capable safety at the moment with options like Cisco 8000 Sequence Safe Routers is the way you construct resilient, future-proof networks. The time to start out your journey towards quantum-safe networking is now.


